Free add-on for your contingency planning
Make Docusnap your central Information Security Management System (ISMS). With automated permission analysis, change tracking, and network visualizations, you can reliably identify security risks and take targeted measures.

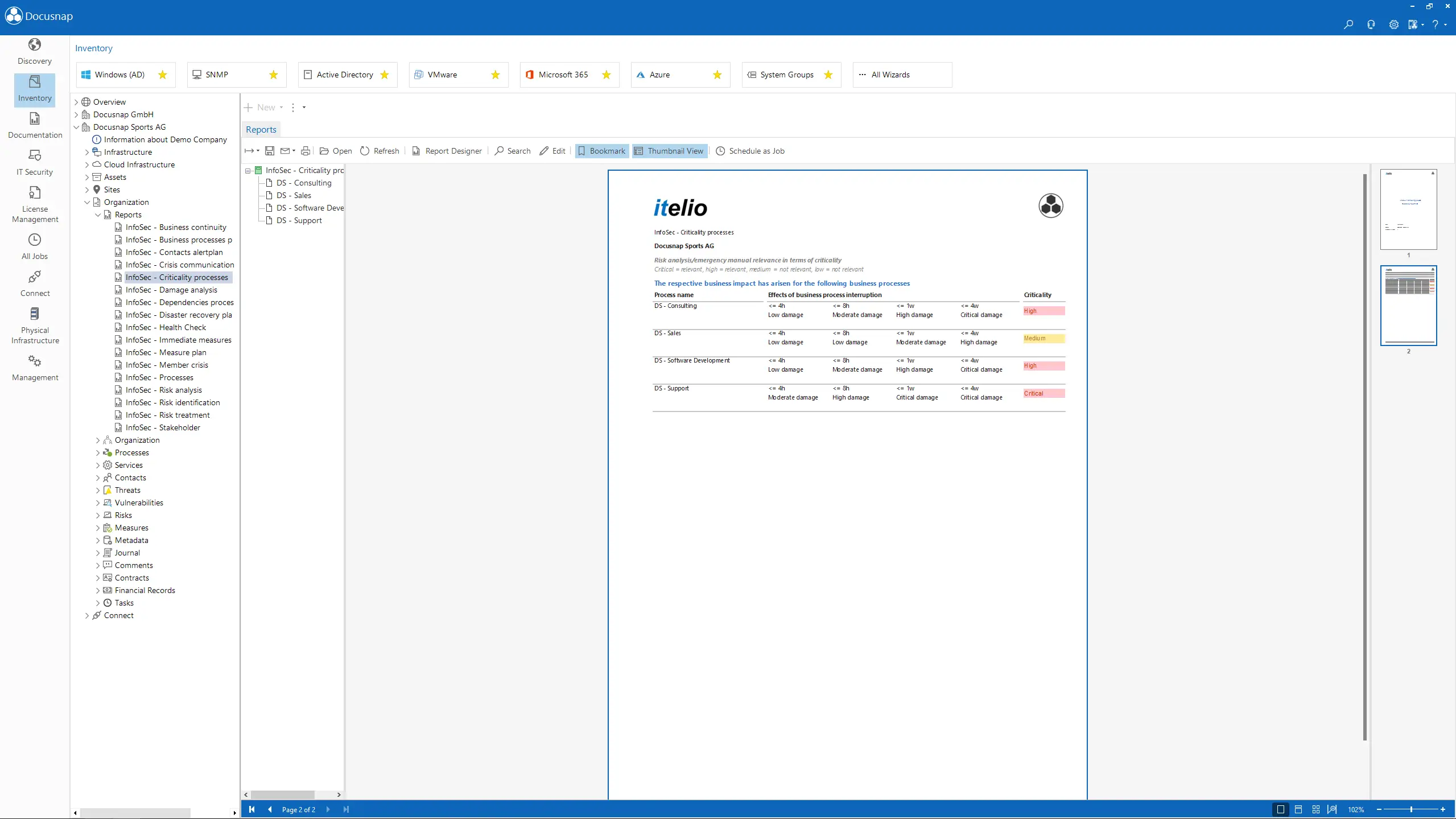
Define which business areas and systems your ISMS should cover, and assess the criticality of those processes. This helps prioritize what must be protected.
Precisely and comprehensively record all systems in your environment. This makes mapping systems to services easier, and supports efficient management.
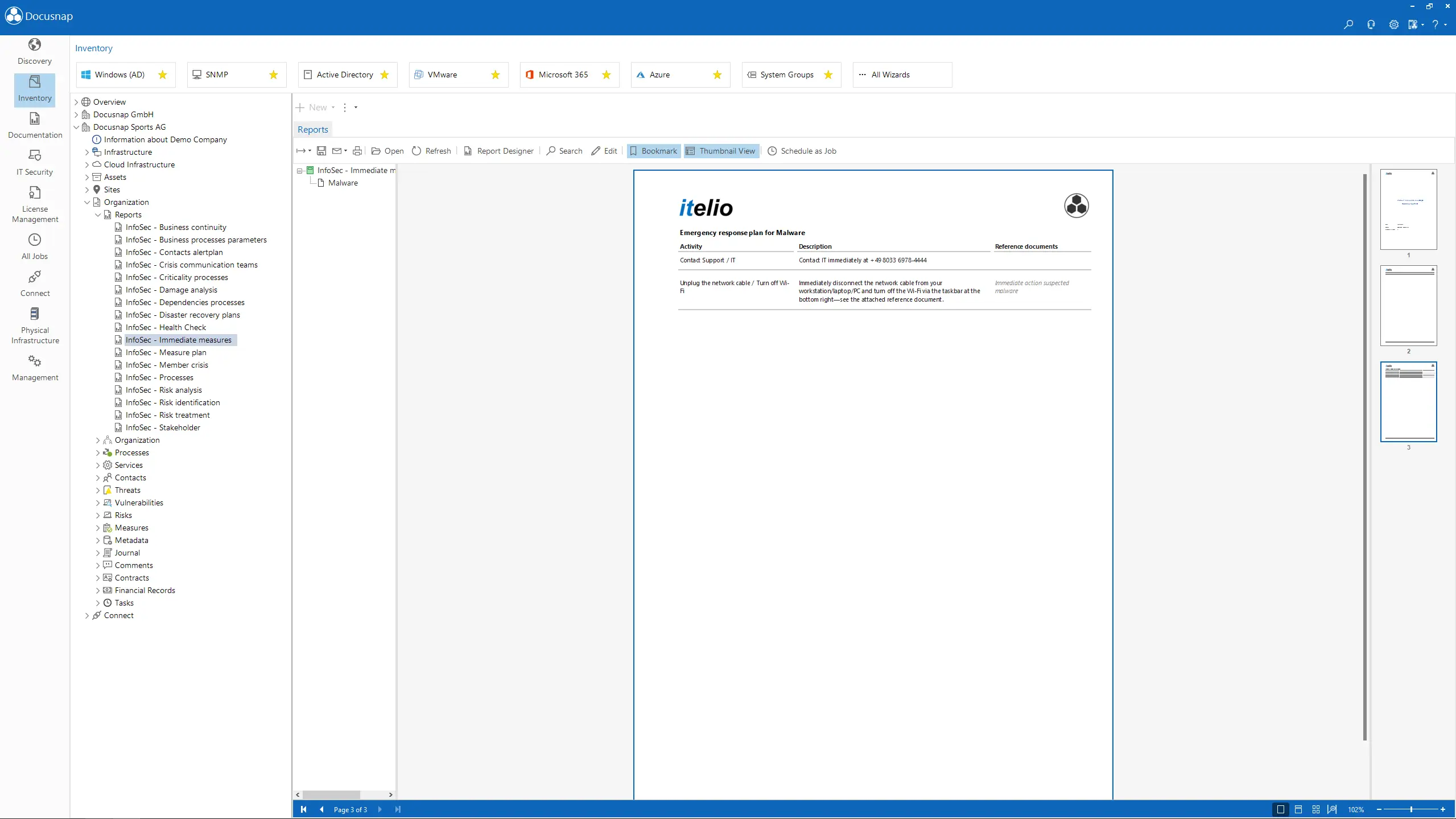
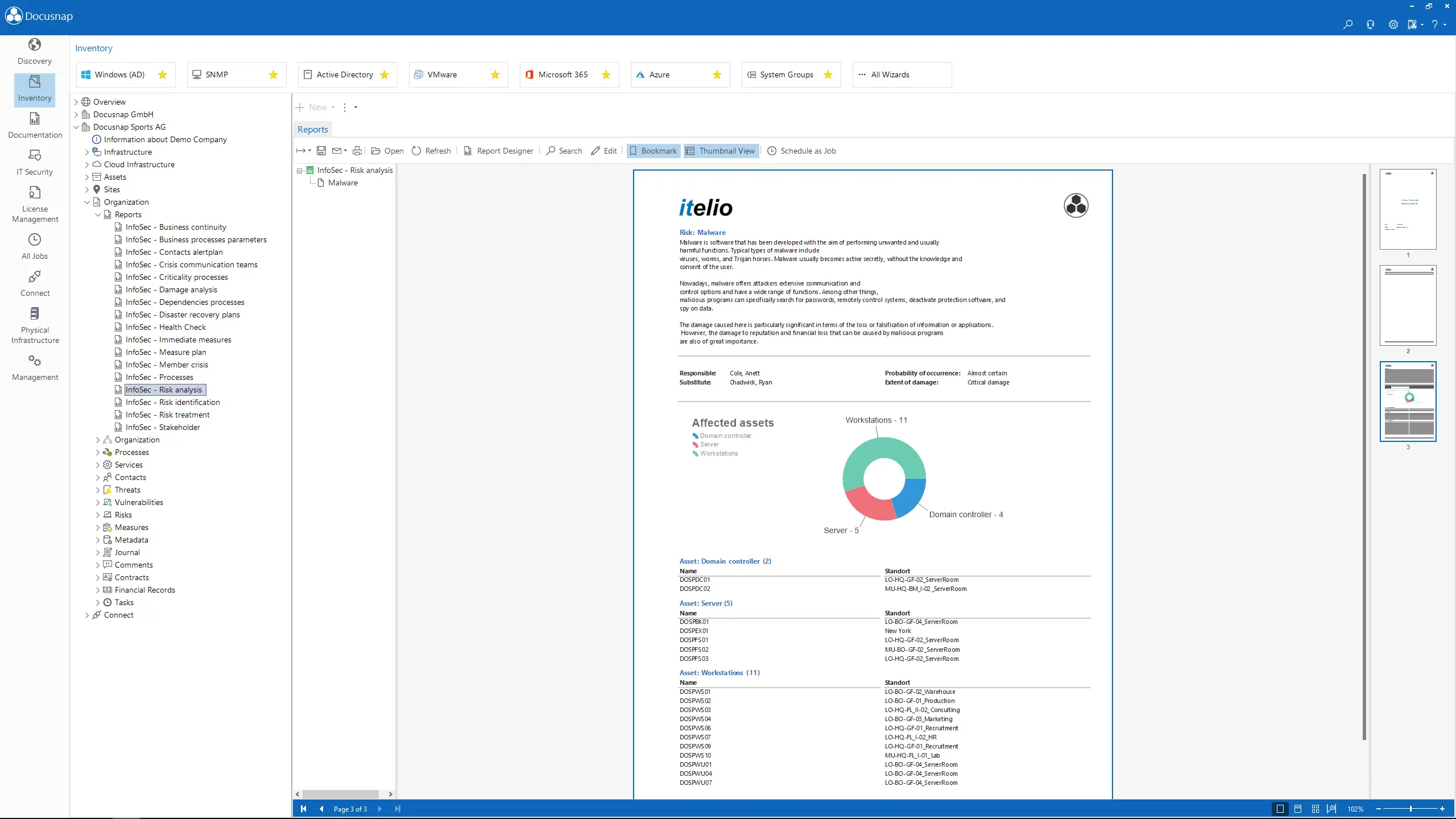
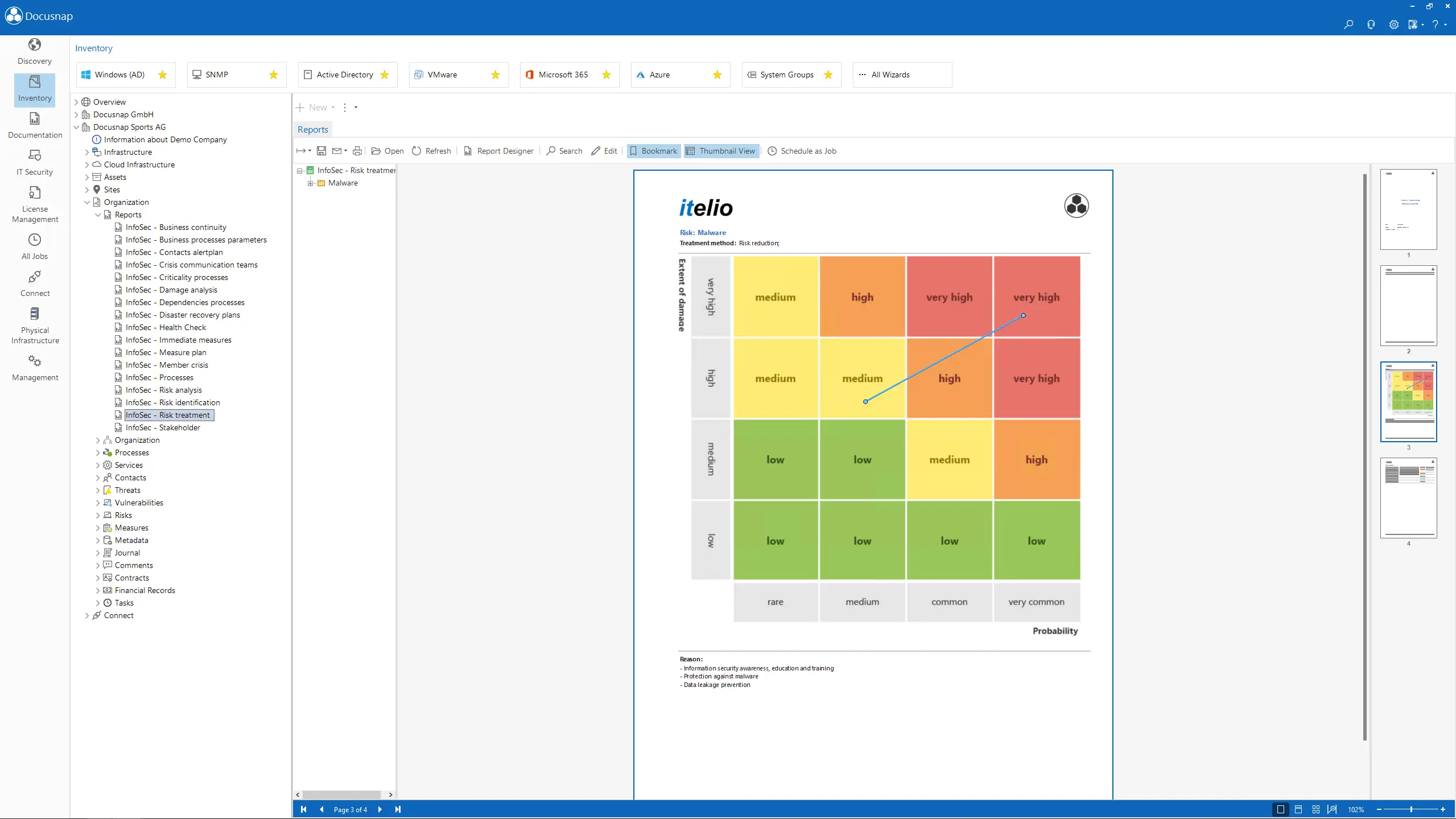
Identify potential risks and vulnerabilities. Based on this, receive concrete suggestions for risk treatment.
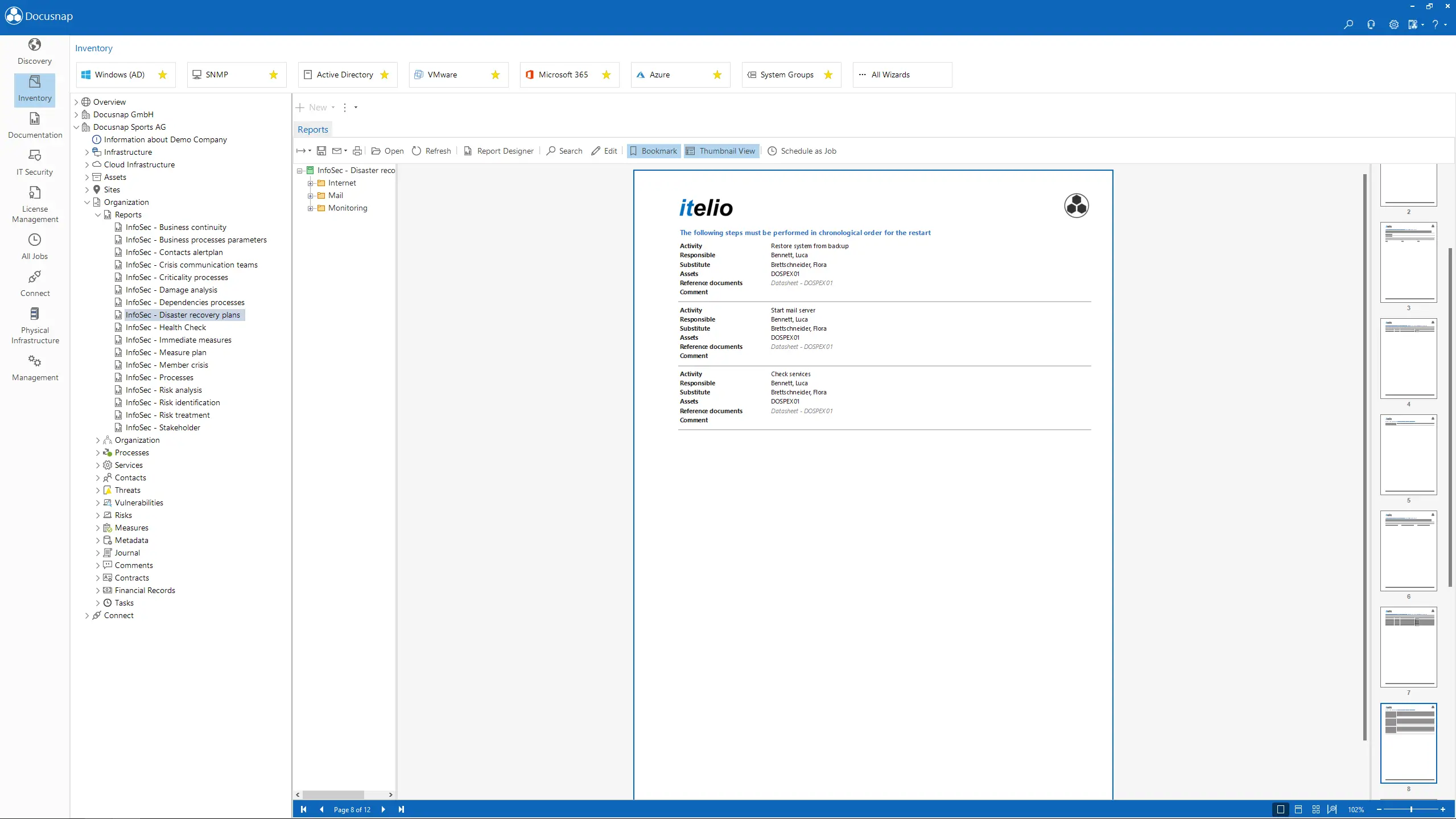
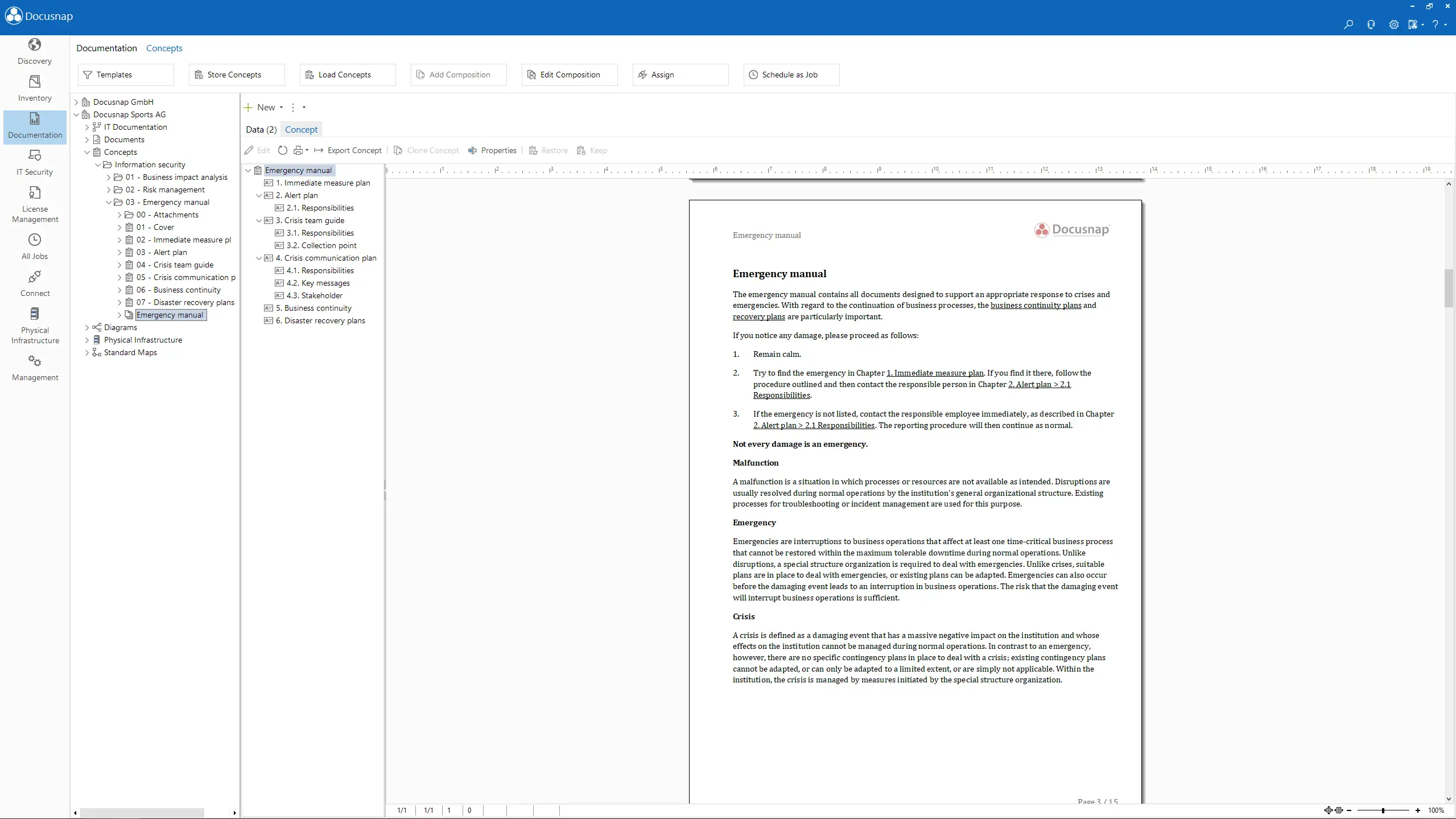
Generate a dynamic IT disaster recovery handbook with clear instructions to restore business operations as quickly as possible. The manual uses data from your inventory and can also be used offline.
What’s New in version 2.4
At Docusnap, we are constantly developing our software to provide you with the best possible support in your everyday IT work. Your requirements and challenges are always our focus: whether it's saving time through automated processes, improving the transparency of your IT infrastructure, or ensuring compliance with regulations—with each new version, we create even more efficient and practical solutions. One example of this is version 2.4 of the “IT contingency planning” add-on. It helps you take targeted action in the event of a crisis and offers even more practical benefits thanks to new functions.
- New inventory tree with data explorer for greater transparency
- Support for implementing NIS 2 requirements through structured recording of relevant content
- Integration of all ISO measures (chapters 4–10) as a guide for information security processes
- Optimized risk analysis and treatment with automatic calculation and visual highlighting of risk values
- Intelligent filter and sorting functions for quick prioritization according to criticality
- Improved input masks for more efficient assignment of risks and services
- Greater stability and user-friendliness thanks to numerous backend and reporting optimizations
The next IT emergency is guaranteed!
It's not a question of if, but when it will happen! So play it safe. Minimize the risks and protect yourself and your IT infrastructure with Docusnap.
Discover the benefits of our add-on
In our video, our expert Kilian gives you a detailed insight into how you can use our add-on to take your information security to the next level — Video only available in German!
IT security solutions from Docusnap

Permission analysis
Centrally monitor user and access rights in Docusnap, analyze rights origin and inheritance to ensure high security standards and prevent unauthorized access.

History
The history function allows you to track changes in the IT system in detail, facilitates the investigation of security incidents, and ensures the traceability of changes.

Visualizations
Docusnap provides you with a comprehensive visualization of your IT network, including all components and dependencies. This allows you to easily identify potential security risks and reliably remedy them.
Contingency planning with Docusnap
Try Docusnap for free
Would you like to test the security features and the IT emergency planning add-on, but don't currently have a valid Docusnap license? No problem—try the software and add-on free of charge for 30 days.
Why is an ISMS so important?
In today's digital world, where information is at the heart of every business and organization, protecting sensitive data is more crucial than ever. With increasing dependence on digital technologies and the ever-growing threat of cybercrime, it is becoming increasingly important to take effective measures and implement an information security management system (ISMS) in a company. Our add-on for emergency planning helps you optimize your company's security and efficiently ward off potential cyber threats.
Legal & regulatory requirements
Companies must comply with certain security standards in order to meet applicable regulations.
Trust of customers and business partners
Only when your data is managed securely can you gain the trust of your customers and business partners.
Constantly emerging cyber threats
Cybercriminals are constantly developing new methods of attack to exploit vulnerabilities in information systems.
Over 5,000 satisfied customers worldwide