The most important thing in brief:
Cyber attacks have long been part of everyday life for IT departments — whether in medium-sized companies or large companies. Instead of focusing exclusively on protecting against threats, the focus is increasingly on the question of How quickly and effectively companies can recover after a cyber incident. This is exactly where the concept of Cyber resilience on. But what does that mean in practice, what makes resilient IT structures stand for — and what role does IT documentation play in this?
Cyber resilience definition
The terms Cyber resilience, cyber resilience and cyber resilience They all refer to the same concept — we use all spellings in the article, as they occur in parallel in everyday life. Cyber resilience is the ability of a company to maintain business operations and recover quickly despite successful cyber attacks or IT disruptions. It is therefore not only a question of prevention, but also of response and adaptability.
Why is cyber resilience important?
IT teams are under constant pressure: Ransomware, phishing, attacks on supply chains or insider threats can never be completely ruled out despite all protective measures. Cyber resilience ensures that companies not only cope with failures, but also emerge stronger as a result. A high level of maturity in cyber resilience therefore not only protects systems, but also reputation, customer trust and legal compliance.
Legislators are an important driver: In addition to IT Security Act and the NIS2 policy In particular, is the upcoming Cyber Resilience Act the EU in focus. It obliges manufacturers and companies to make their products and processes resilient over the entire life cycle. More details about the requirements and effects can be found in our separate blog article on Cyber Resilience Act.
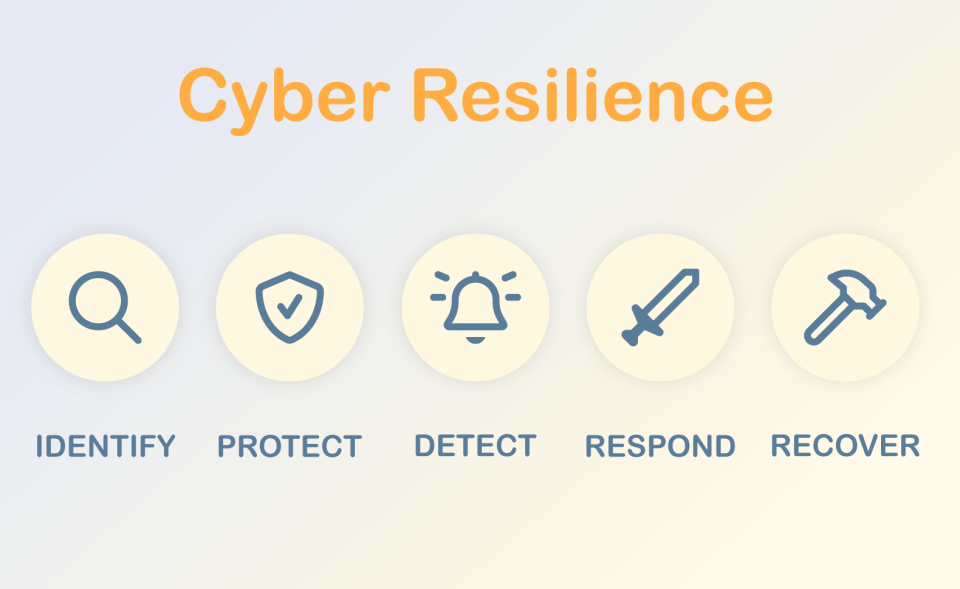
The 5 pillars of cyber resilience
If you want to anchor cyber resilience in the long term, you should focus on five basic pillars: Prepare & Identify, Protect, Detect, Respond, and Recover. This framework helps companies to holistically build their cybersecurity approach — and to continuously develop it in the face of new threats and growing requirements
Measures to improve cyber resilience
- Regular security audits and penetration tests
- Sensitization of employees (security awareness)
- Network segmentation & zero trust approaches
- Redundant systems and offsite backups
- Establishment of a crisis team and emergency handbook
- Use of SIEM and monitoring tools
These measures aim to: cyber resilience to strengthen holistically — from technology to processes to people.
What are the 7 steps to cyber resilience?
- Risk identification & assessment
→ Risks and vulnerabilities across the entire IT landscape are identified, evaluated and prioritized in order to derive targeted measures. - Implement protective measures
→ Based on the risk analysis, technical (e.g. firewalls, access controls) and organizational protective measures are implemented to make attacks more difficult. - Establish monitoring and threat detection
→ Continuous monitoring and automated detection systems (e.g. SIEM) help to identify and limit security incidents at an early stage. - Plan an incident response
→ Clear processes, roles and communication channels are defined so that you can react quickly and in a controlled manner in an emergency. - Ensuring business continuity (BCM)
→ Business continuity plans ensure that critical business processes continue running or can be quickly restored even in the event of a crisis. - Build recovery capacity (disaster recovery)
→ Robust backup and recovery strategies ensure that systems and data can be restored reliably and quickly after an incident. - Follow-up & continuous optimization
→ After an incident, processes are analyzed, weak points identified and improvements implemented to permanently increase resilience.
How Docusnap helps you with your cyber resilience
Docusnap creates transparency about your IT infrastructure — the basis of every cyber resilience strategy. By automatically inventoriing, documenting and visualizing networks, servers, clients and authorizations, Docusnap provides all the information you need for risk analyses, emergency plans, recovery plans, or verification requirements. Whether creating a network plan in case of a crisis, documenting backup infrastructures, or analyzing critical dependencies — Docusnap helps you keep track before Something is happening.
Practical example: A company was crippled by a ransomware attack. Thanks to the infrastructure documented with Docusnap — including exact network plans, role and rights overviews, and backup paths — the IT team was able to quickly understand which systems were affected, set priorities and carry out the restart in a structured manner.
Conclusion
Cyber resilience is much more than just another buzzword in the IT security world. Companies today must assume that attacks or disruptions do not preventable, but controllable must be. If you are resilient, you minimize downtime, protect business processes and gain a decisive competitive advantage in times of crisis.
Tip: Read our blog article on the current “Cyber Resilience Act.”
The next steps:
If you want to increase the maturity level of your cyber resilience, you need transparency about your own IT landscape in particular. This is exactly where Docusnap comes in. Get to know our solution without obligation and test all functions related to IT inventory and documentation.
Try it now for free!


