The most important thing in brief:
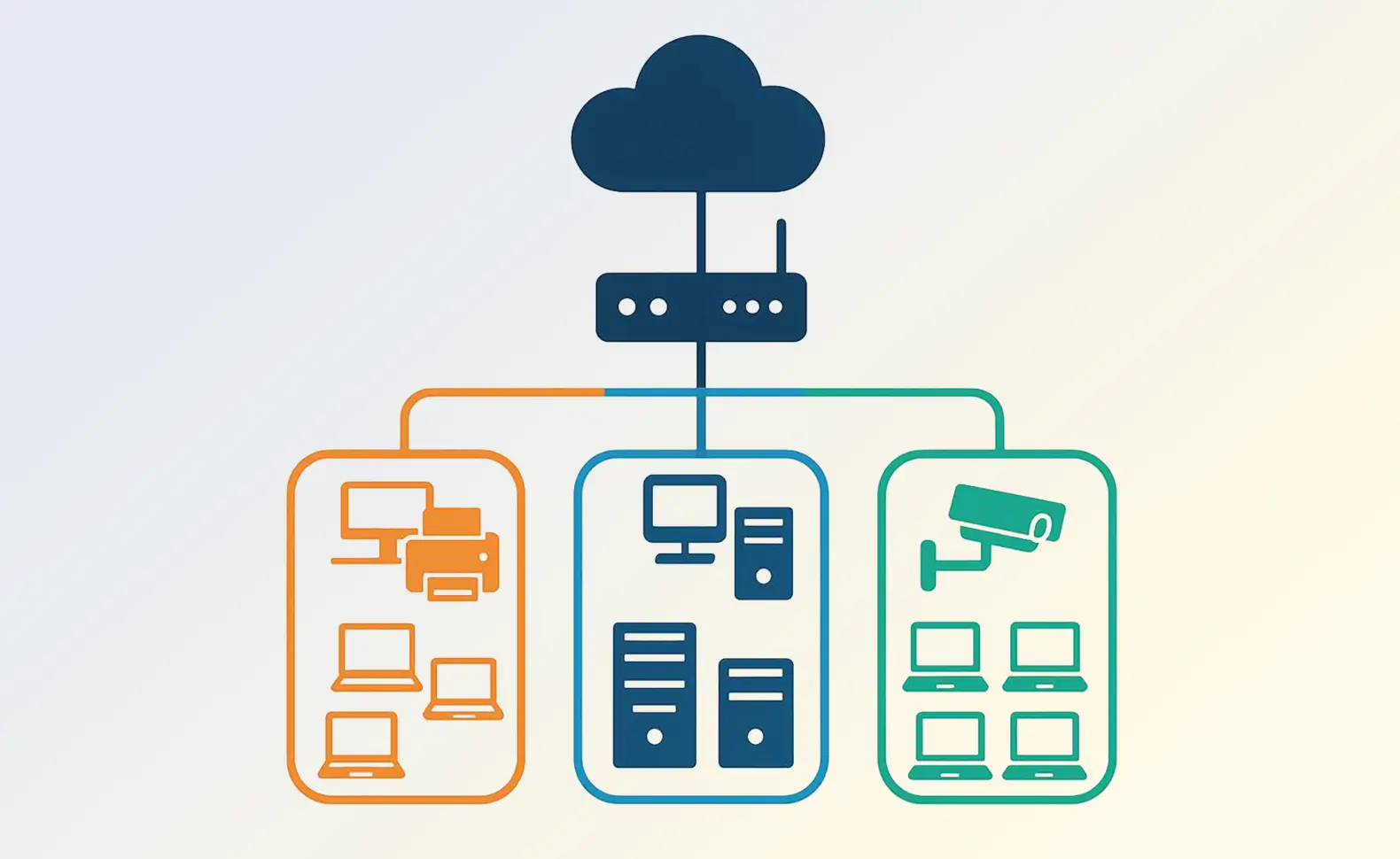
What is network segmentation?
Network segmentation describes the division of a large network into smaller subnetworks (segments). Each segment is isolated from one another by technical measures and can have its own security guidelines. Technically, this is done, for example, via VLANs (virtual local area networks), firewalls or software-defined networking (SDN).
Network segmentation goals
- Security enhancement: Attackers are prevented from moving sideways across the network.
- Performance optimization: Data traffic within a segment is reduced and made more efficient.
- Compliance and data protection: Statutory requirements such as GDPR or industry-specific standards (e.g. ISO 27001, BSI IT basic protection) require the protection of critical data.
Why is network segmentation necessary?
In addition to security and compliance aspects, the growing complexity of modern IT landscapes also plays a role. Companies today use hybrid infrastructures of on-premises servers, cloud services and mobile devices. Without segmentation, administrators quickly lose visibility and expose their organization to increased risk. Structured segmentation creates transparency and predictable security here.
Focus on safety
Cyber attacks are becoming increasingly sophisticated. Ransomware in particular aims to spread across the entire network. Through segmentation, so-called “East-West Movements” significantly restrict from attackers.
Statutory requirements
- BSI basic IT protection: Recommends dividing critical networks into safety zones.
- ISO/IEC 27001: Requires appropriate technical and organizational measures to control access.
- GDPR: Requires that personal data be protected from unauthorized access — segmentation is a practical way.
A risk that many companies are aware of
A single careless click on a malicious email attachment can be enough to paralyze an entire corporate network. Malware spreads in fractions of a second if there are no effective barriers. Right here comes the network segmentation into the game. It ensures that even in the event of an attack, the damage remains localized and does not endanger the entire company. Here is an example from practice: A hospital operates a variety of medical devices, administrative PCs and patient databases. Without segmentation, an infected office PC could potentially paralyze the entire system. Through targeted network segmentation, medical devices are strictly separated from administrative networks. In this way, an attack on a single area remains localized, while critical systems such as ventilators or patient databases remain functional. This example impressively shows why segmentation is an indispensable security measure today.
How is network segmentation implemented?
Implementation depends heavily on the network architecture, but usually follows these steps:
- Infrastructure analysis: Recording of all systems, data flows and dependencies.
- Definition of safety zones: Critical systems (e.g. databases, production networks) are separated from less sensitive areas (e.g. guest WLAN).
- Technical implementation: Use of VLANs, firewalls, access control lists (ACLs), or microsegmentation via SDN.
- Monitoring and documentation: Without ongoing monitoring and up-to-date documentation, segmentation quickly loses its effectiveness.
What should be considered during implementation?
- Clear segmentation goals: Not every department needs its own segment. Instead, data flows and security risks should be analyzed.
- Ease of use: Too strict segmentation can hinder work processes. A balance of safety and efficiency is crucial.
- Regular update: Networks are constantly changing. New systems, devices, or cloud services must be considered on an ongoing basis.
- Transparency: Without an overview, companies risk uncontrolled “shadow IT.”
Benefits of network segmentation
1. Increased safety
A compromised system is limited to one segment. Attackers can no longer freely operate across the entire network.
2. Better performance
Less broadcast traffic and targeted data flow increase network speed.
3. Simplified compliance
Compliance with legal regulations is significantly facilitated by clearly defined safety zones.
4. Transparency and control
With tools like Docusnap, IT departments can identify risks more quickly and implement effective measures.
5. Cost reduction
Fewer outages due to attacks and more efficient management of the IT infrastructure lead to savings in the long term.
Network segmentation combined with Docusnap
The introduction and maintenance of a segmentation strategy is complex without suitable tools. Docusnap makes the entire process easier:
- Automated inventory: Overview of all devices, servers, and applications on the network.
- Visualization: Automatically generated network plans show segments and connections at a glance.
- Authorization management: Who has access to which data? With Docusnap, this can be presented and controlled transparently.
- Compliance Support: Current documentation ensures tests and audits significantly simplified.
Conclusion
Network segmentation is a central element of modern IT security strategies. It protects companies from the uncontrolled spread of attacks, improves performance and supports regulatory compliance. Especially in times of increasing cyber threats, segmentation is no longer an option but a must. With a solution such as Docusnap Companies can not only present their networks transparently, but also efficiently plan, document and monitor segmentation measures. This sustainably strengthens safety — without restricting employee productivity.
FAQs
The next steps:
With targeted network segmentation, you create security, increase the performance of your systems and lay the basis for a stable, future-proof IT infrastructure. Docusnap provides you with the necessary transparency and documentation to efficiently plan, implement and successfully operate segmentations in the long term.
Try it now for free!


