The most important thing in brief:
- Definition: A VLAN (virtual local area network) logically segments a physical LAN to reduce broadcast load and strictly segregate access.
- Benefit: Less broadcast traffic and significantly higher security thanks to clearly defined network zones.
- Tool tip: Docusnap automatically inventories VLAN IDs and port assignments — changes are immediately documented and traceable.

What is a VLAN?
A Virtual Local Area Network (VLAN) is a logically segmented sub‑network inside a physical Layer‑2 network. Instead of installing separate switch hardware for every department, administrators can use IEEE 802.1Q VLAN tagging to separate broadcast domains in software. The resulting VLAN network runs over the same cables and switches but behaves as if each segment were on its own infrastructure.
VLAN explained simply: A VLAN is like a virtual room inside a network that groups devices logically—no new cables required.
Why are VLANs necessary?
- Network segmentation & broadcast reduction
In large environments, ARP and broadcast frames flood every port. A well‑designed VLAN layout limits broadcast domains to a few dozen hosts, cutting load and boosting stability. - Security benefits & role separation
A guest Wi‑Fi is a classic example: employee devices may access internal servers, guests may not. A dedicated GUEST VLAN strictly limits access while a firewall handles inter‑VLAN routing. Industry regulations (e.g., PCI DSS in payments) also require logical segmentation—VLANs meet this need and help spatially isolate sensitive data for GDPR compliance. - Legal aspects
The EU’s GDPR demands appropriate technical and organisational measures to protect personal data. A strictly separated production VLAN ensures only authorised devices gain access. A VLAN plan can also define monitoring (NetFlow, IDS) to simplify forensic analysis.
Setting up a VLAN network: step‑by‑step
Whether you are designing a brand‑new VLAN layout or modernising an existing one, this guide helps you succeed.
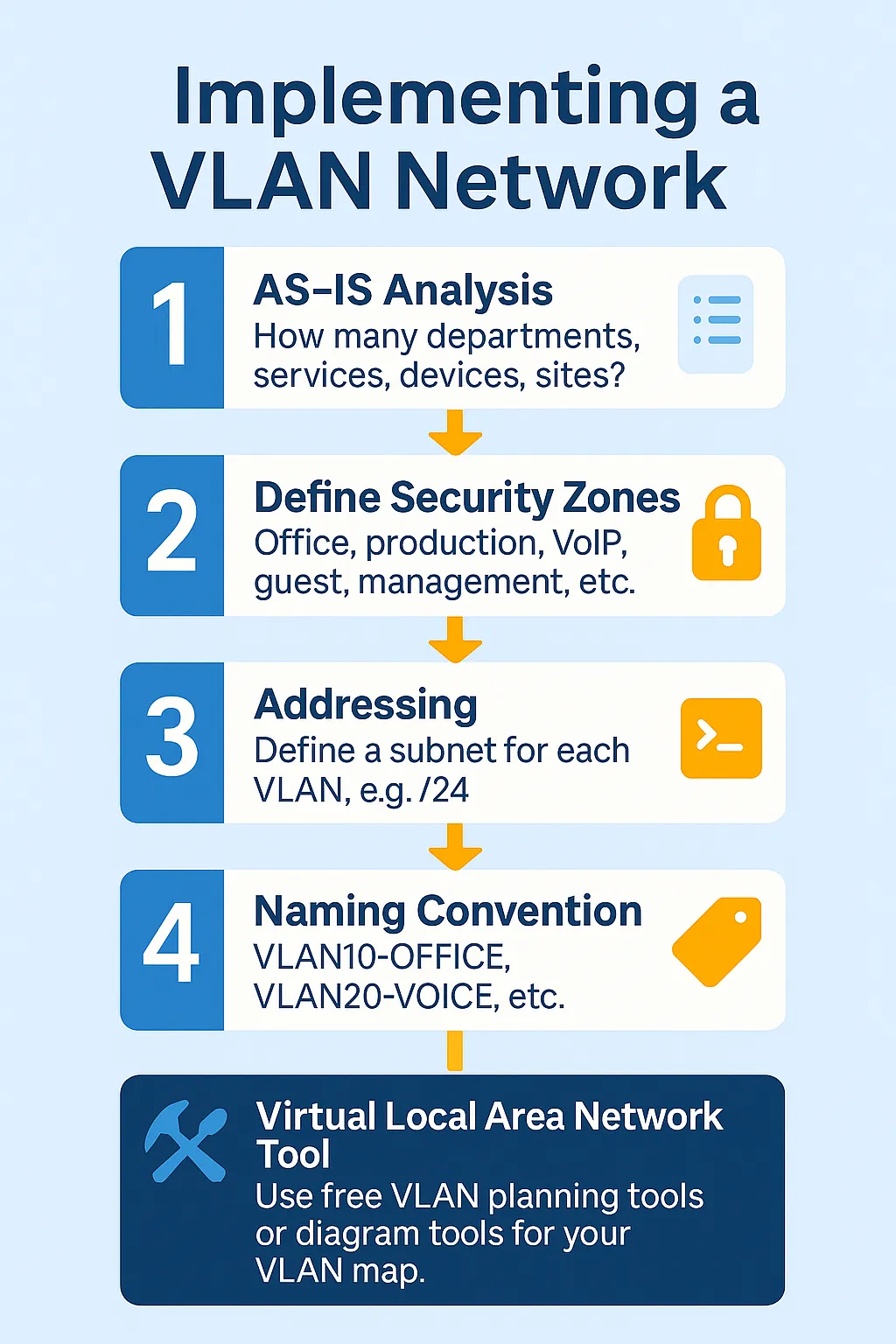
Step 1 – Plan and implement your VLAN network
- AS‑IS analysis: How many departments, services, devices, sites?
- Define security zones: Office, production, VoIP, guest, management, etc.
- Addressing: Assign a subnet to every VLAN, e.g. /24.
- Naming convention: VLAN10_OFFICE, VLAN20_VOICE, etc.
- VLAN planning tool: Use free VLAN‑planning or diagram tools to create your map.
Tip: A clean VLAN plan prevents tagging and routing errors. The more complex the topology, the more important a clear naming scheme.
Step 2 — Configure Switch VLAN
- Access port — the simple terminal connection
An access port only ever belongs to one VLAN and sends packets untagged. The device therefore does not have to have a VLAN function.
stake: Office PCs, server NICs, printers
Merke: Access = untagged — Frames leave the port without a VLAN tag. - Trunk port — The multi-lane line between switches
A trunk port transports multiple VLANs simultaneously. The Switch attaches a 4-byte tag to each frame in accordance with IEEE 802.1Q so that the other party knows which VLAN the packet belongs to.
stake: Uplinks between switches, firewall or router connections, virtualization hosts
Merke: trunk = Tagged — multiple VLANs on one port.
Step 3 — Enable inter-VLAN routing
Inter-VLAN routing is required to exchange data between VLANs.
- Layer 3 Switch with Switched Virtual Interface (SVI)
The Switch receives a separate virtual interface for each VLAN.
instance:Interface Vlan10 ip address 10.0.10.1 255.255.255.0
Gateway: Devices in VLAN 10 use 10.0.10.1. - External firewall/router via trunk line
All VLANs are tagged (e.g. eth0.10, eth0.20) LED to a dedicated firewall.
Vantage: Centralized security and filtering rules in one place.
typical: Next-gen firewall with DPI or IDS/IPS.
Both methods serve the same purpose, but differ in performance, range of functions, and administration costs. Smaller sites often prefer the simplicity of a Layer‑3 switch; larger sites value the granular control of a central firewall.
Step 4 — Safety Hardening & Monitoring
- ACLs: Block unnecessary east‑west traffic; confine compromised clients to their zone.
- DHCP Snooping & Dynamic ARP Inspection: Stop rogue DHCP servers and forged ARP replies.
- Syslog & NetFlow: Collect configs and traffic logs centrally for audits, capacity planning and forensics.
Step 5 — Documentation & Maintenance
Export the VLAN map (PDF or Visio) after every change, store it in the central config repository and update it immediately whenever the topology changes.
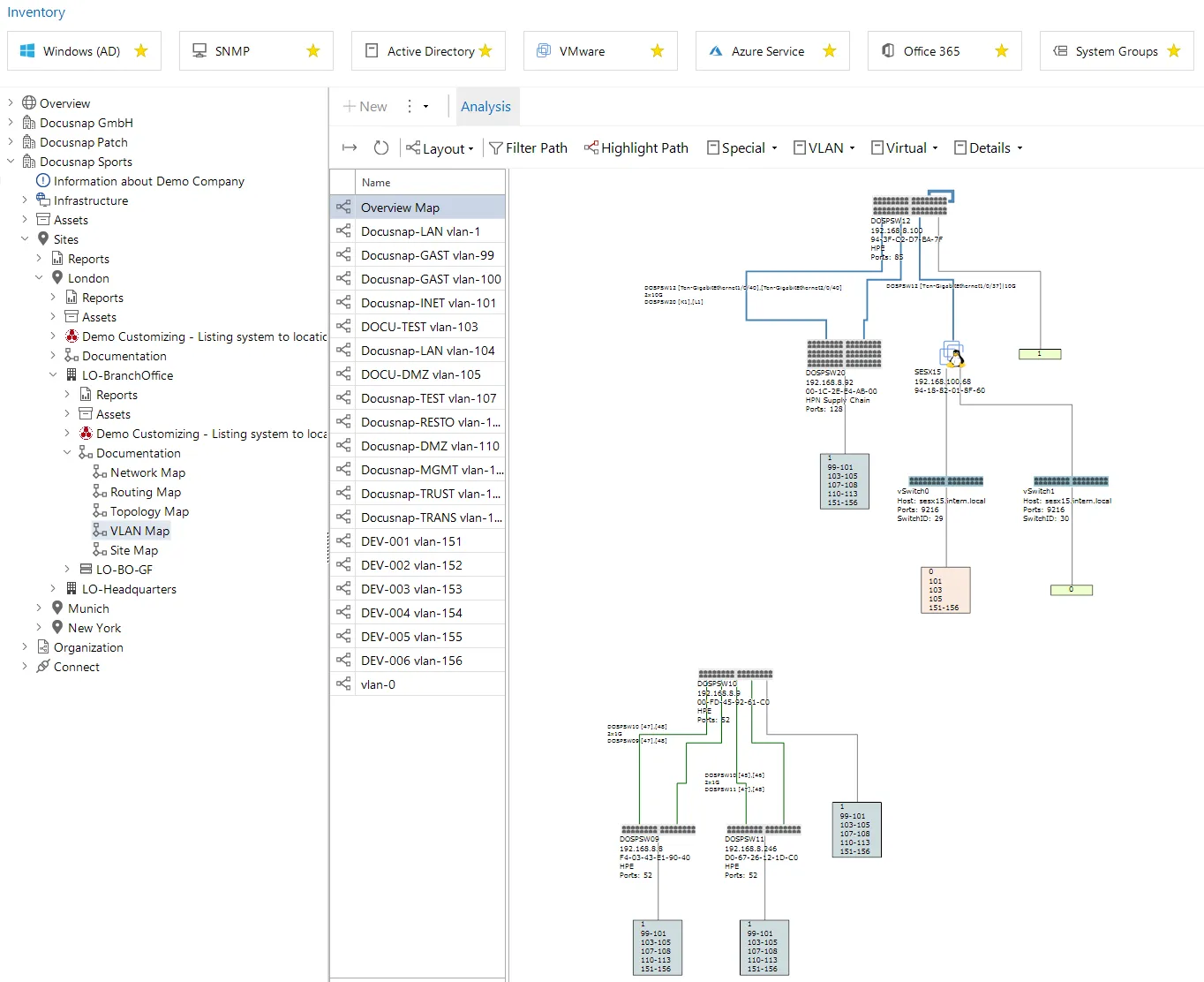
VLAN inventory & documentation with Docusnap
Docusnap automates much of the work. Via SNMP walks and Windows WMI, it reads all switch configs, builds an up‑to‑date VLAN inventory, and shows tagged/untagged information in clear diagrams. Continuous discovery means the visual network plan stays current without manual updates. The topology function automatically illustrates relationships between switch ports, trunks and access ports.
Practical example: From chaos to a structured VLAN network
Scenario: A medium-sized machine manufacturer operates production, administration and customer WLAN on the same Layer-2 network. 150+ devices cause broadcast storms, and worms scan the network unhindered at night.
Solution using VLANs:
- Division into six VLANs: Office (10), Production (20), CNC machines (30), VoIP (40), Management (50), Guests (60).
- VLAN planning tool for inventory.
- New core switches with layer 3 routing.
- Firewall rules: Guests → Internet only | Production → ERP, no Internet.
Outcome: 95% less broadcast traffic, malware can no longer move laterally, GDPR compliance confirmed
Common mistakes & how to avoid them
Problem: device on the wrong network
Cause: Port not tagged
Solution: Port not taggeUse port templates & automate provisioning
Problem: Duplicate VLAN IDs
Cause: Overlaps in Site Connectivity
Solution: Create a global ID matrix and check it before activation
Issue: Spanning Tree Disabled
Cause: Layer 2 Loops & Broadcast Storms
Solution: consistently activate RSTP/MSTP
Problem: VoIP jitter
Cause: Voice VLAN not disconnected or QoS is missing
Solution: Set separate VLAN ID & DSCP tag
Conclusion
A VLAN is much more than just an elegant network gimmick. When implemented correctly, it forms the basis for scalability, security, and compliance in modern infrastructures. With a clear plan strategy, the right tools, and consistent documentation, you can get the most out of your network.
FAQs
Next steps
Try Docusnap as a VLAN discovery tool free of charge and without obligation for 30 days — try it now!
Try it now


