- Try it
- Products
- Use cases
- Use cases
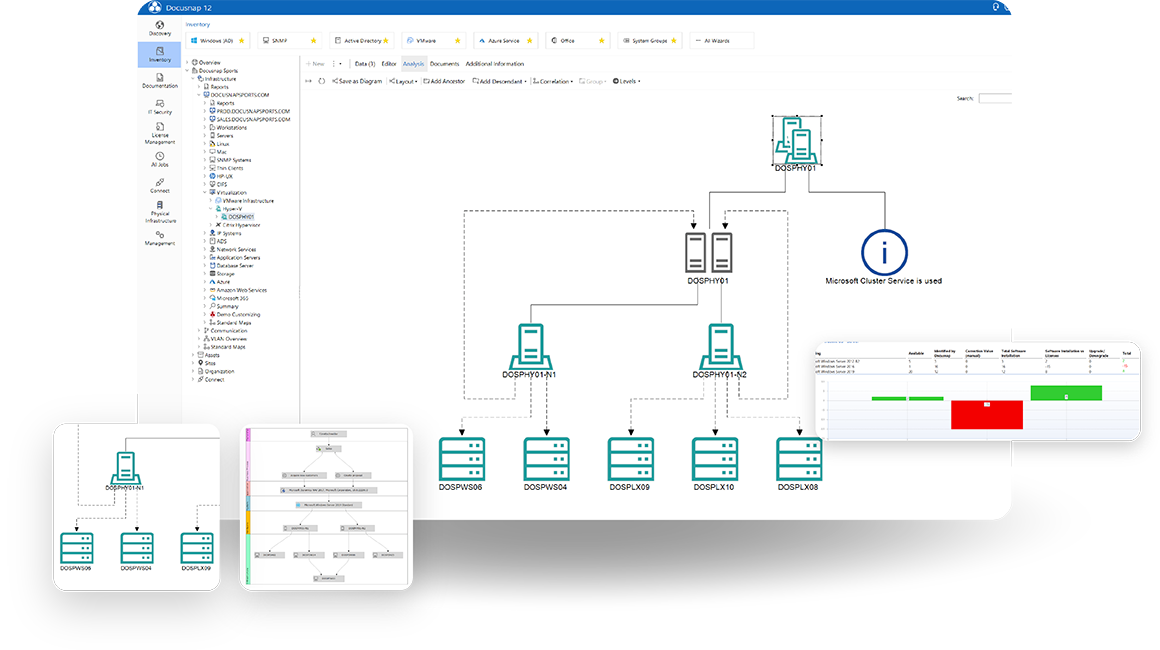
- Docusnap for your ITDocusnap365 for your IT! The automatic inventory and documentation features save IT administrators a great deal of time-consuming and labor-intensive tasks in their daily work. Self-generated reports and maps provide a constantly updated overview of the IT network, enabling IT and business managers to make informed decisions. By constantly monitoring security-relevant systems, IT security officers can quickly track changes and ensure that all systems are up to date.
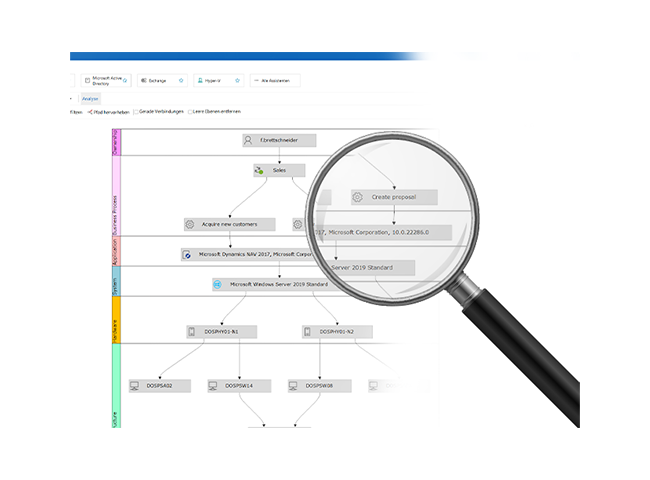
- IT administratorIT documentation easier than ever! With Docusnap you automate time-consuming inventory and documentation tasks. The software regularly inventories your entire IT network and provides you with all the information in clear reports and maps. Use this up-to-date data to make your IT operations more efficient and secure.
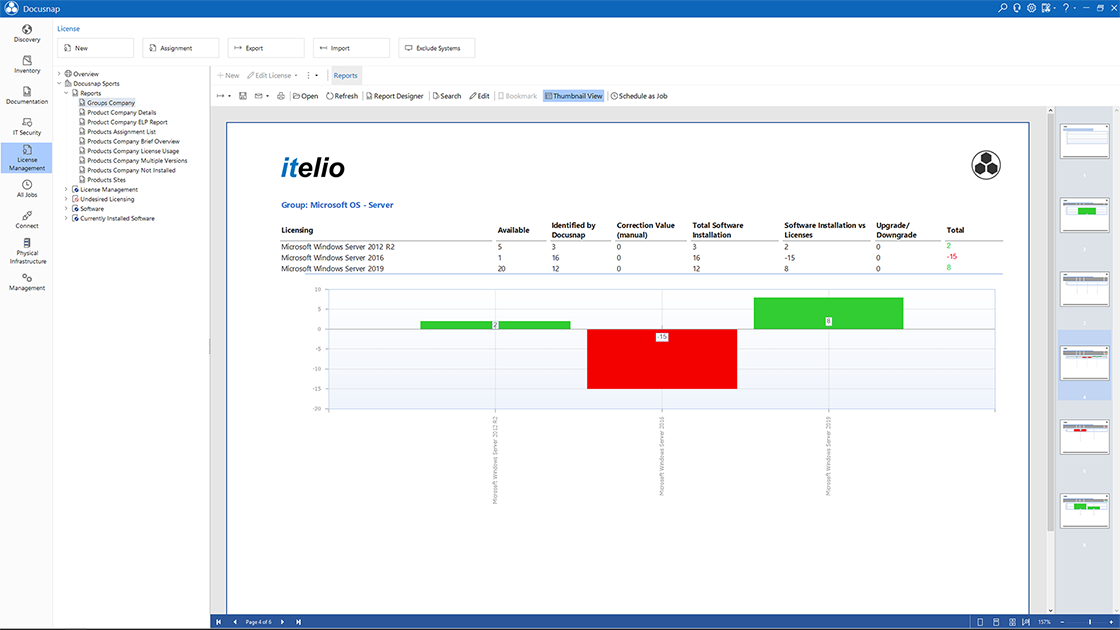
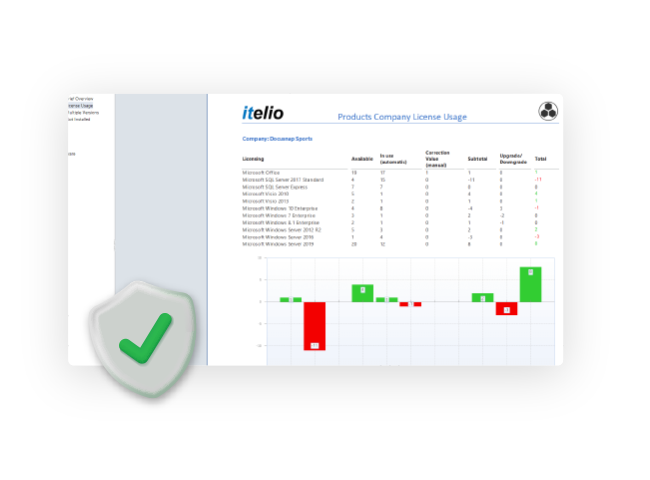
- IT managerAn up-to-date overview saves time and money! Docusnap automatically and regularly provides you with complete overviews and meaningful summaries of your IT. Use this knowledge to optimize your processes and save costs. Only those who know their IT can make informed decisions.
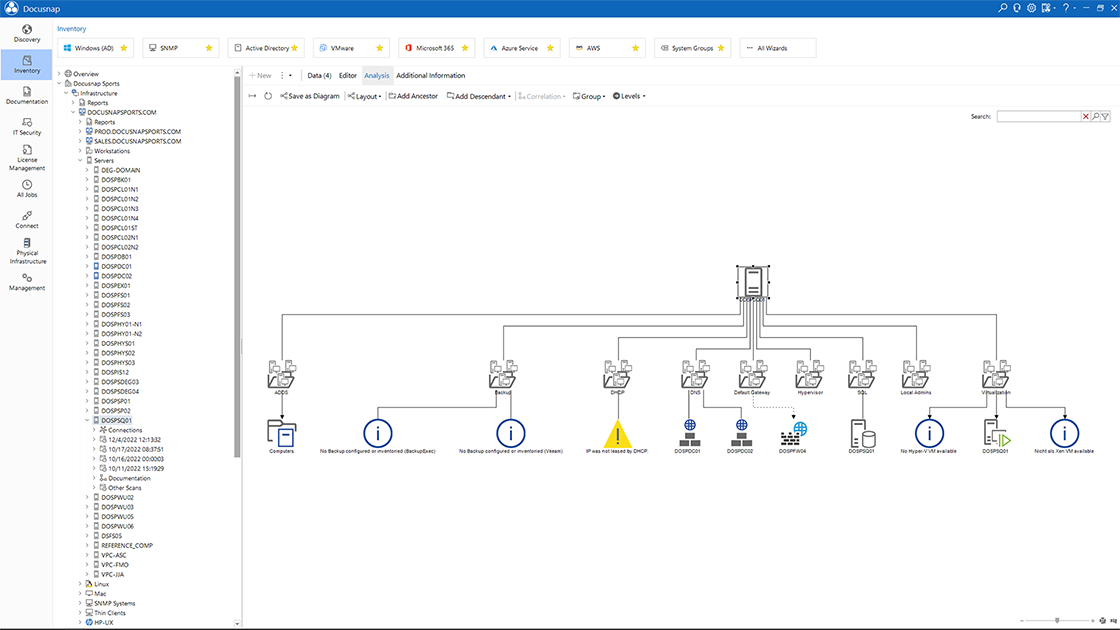
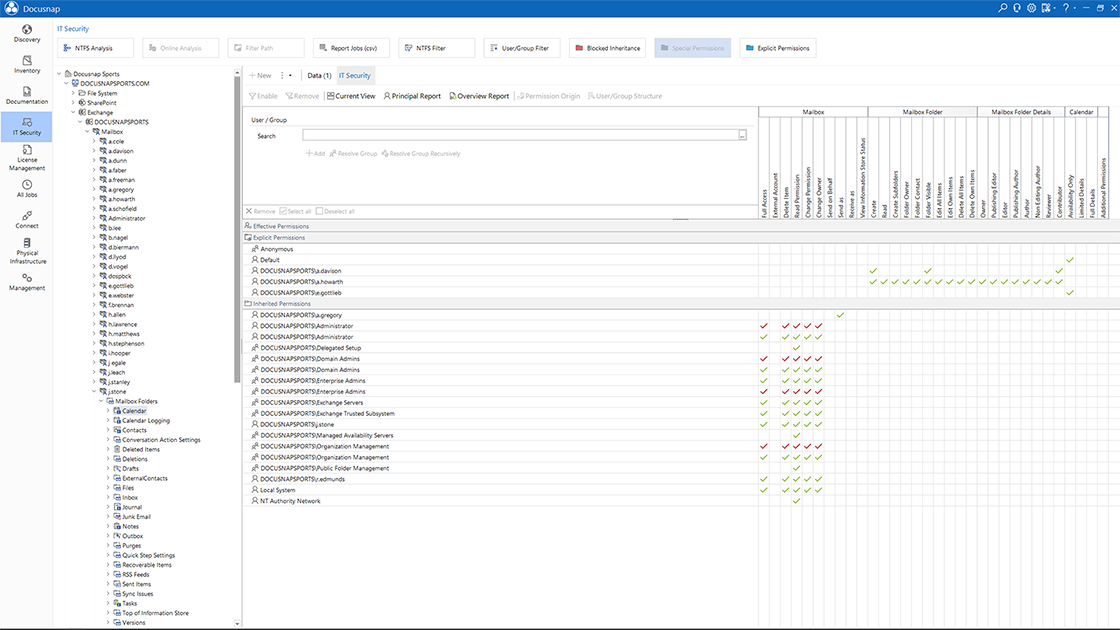
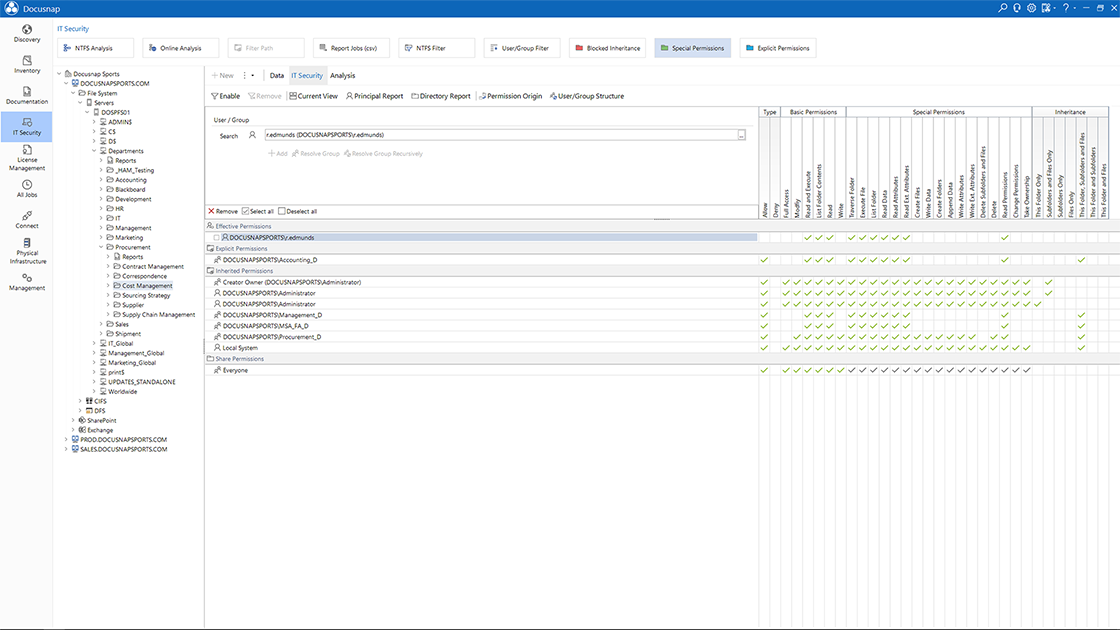
- IT security officerIT security at a glance! To ensure a high level of IT security, you need to consider many different aspects, such as user permissions, software and OS statuses, or firewall configurations. With the help of Docusnap, you have all this information in one central place. In addition, thanks to regular network inventory, all data is always up to date.
- Docusnap for businessDocusnap and Docusnap365 as drivers for your business! Docusnap is the leading software for automated IT inventory, documentation and analysis – and has been since 2004. Docusnap365 continues this tradition in the cloud. There are many ways you can use the software to enhance your business. Everyone knows the importance of having up-to-date and complete IT documentation, but few people own it. Therefore, offer to create it for the customer or install Docusnap at the customer’s site and run it if necessary. This will open doors for you with new customers and strengthen relationships with existing customers.
- Customer documentationIT documentation as a service! Docusnap and Docusnap365 independently collect the network data of all your customers and make it available to you via a secure online connection. The software automatically creates predefined documents and maps, even in your customers’ corporate design if desired. This saves you time and effort and creates trust with the customer.
- New customer salesGain new customers with Docusnap! Cold calling is usually very frustrating. With Docusnap and Docusnap 365, you have powerful arguments that open doors. Almost no customer has up-to-date IT documentation, although everyone knows that it is very important for many reasons. Therefore, offer the creation of IT documentation for a contribution towards expenses. This is the first step and follow-up orders can be generated using the Docusnap data.
- Existing customer salesOptimize your customer relationship! With the help of Docusnap and Docusnap365, you have a holistic overview of your customers’ IT networks. This makes it very easy for you to uncover security gaps and need for action. In this way, you increase your customers’ IT security and ensure follow-up orders at the same time.
- Customer projectsSecure IT projects with Docusnap! Docusnap and Docusnap365 provide an exact ACTUAL state of the IT network. This makes it very easy to define concrete project goals and identify potential obstacles in advance. In addition, the regular inventories enable detailed change and progress tracking. Therefore, IT projects become more successful and less expensive.
- Docusnap for your ITDocusnap365 for your IT! The automatic inventory and documentation features save IT administrators a great deal of time-consuming and labor-intensive tasks in their daily work. Self-generated reports and maps provide a constantly updated overview of the IT network, enabling IT and business managers to make informed decisions. By constantly monitoring security-relevant systems, IT security officers can quickly track changes and ensure that all systems are up to date.
- Use cases
- Use cases
- Training
- Support
- Shop
- Partner
- Login
- Try it
- Products
- Use cases
- Use cases
- Docusnap for your ITDocusnap365 for your IT! The automatic inventory and documentation features save IT administrators a great deal of time-consuming and labor-intensive tasks in their daily work. Self-generated reports and maps provide a constantly updated overview of the IT network, enabling IT and business managers to make informed decisions. By constantly monitoring security-relevant systems, IT security officers can quickly track changes and ensure that all systems are up to date.
- IT administratorIT documentation easier than ever! With Docusnap you automate time-consuming inventory and documentation tasks. The software regularly inventories your entire IT network and provides you with all the information in clear reports and maps. Use this up-to-date data to make your IT operations more efficient and secure.
- IT managerAn up-to-date overview saves time and money! Docusnap automatically and regularly provides you with complete overviews and meaningful summaries of your IT. Use this knowledge to optimize your processes and save costs. Only those who know their IT can make informed decisions.
- IT security officerIT security at a glance! To ensure a high level of IT security, you need to consider many different aspects, such as user permissions, software and OS statuses, or firewall configurations. With the help of Docusnap, you have all this information in one central place. In addition, thanks to regular network inventory, all data is always up to date.
- Docusnap for businessDocusnap and Docusnap365 as drivers for your business! Docusnap is the leading software for automated IT inventory, documentation and analysis – and has been since 2004. Docusnap365 continues this tradition in the cloud. There are many ways you can use the software to enhance your business. Everyone knows the importance of having up-to-date and complete IT documentation, but few people own it. Therefore, offer to create it for the customer or install Docusnap at the customer’s site and run it if necessary. This will open doors for you with new customers and strengthen relationships with existing customers.
- Customer documentationIT documentation as a service! Docusnap and Docusnap365 independently collect the network data of all your customers and make it available to you via a secure online connection. The software automatically creates predefined documents and maps, even in your customers’ corporate design if desired. This saves you time and effort and creates trust with the customer.
- New customer salesGain new customers with Docusnap! Cold calling is usually very frustrating. With Docusnap and Docusnap 365, you have powerful arguments that open doors. Almost no customer has up-to-date IT documentation, although everyone knows that it is very important for many reasons. Therefore, offer the creation of IT documentation for a contribution towards expenses. This is the first step and follow-up orders can be generated using the Docusnap data.
- Existing customer salesOptimize your customer relationship! With the help of Docusnap and Docusnap365, you have a holistic overview of your customers’ IT networks. This makes it very easy for you to uncover security gaps and need for action. In this way, you increase your customers’ IT security and ensure follow-up orders at the same time.
- Customer projectsSecure IT projects with Docusnap! Docusnap and Docusnap365 provide an exact ACTUAL state of the IT network. This makes it very easy to define concrete project goals and identify potential obstacles in advance. In addition, the regular inventories enable detailed change and progress tracking. Therefore, IT projects become more successful and less expensive.
- Docusnap for your ITDocusnap365 for your IT! The automatic inventory and documentation features save IT administrators a great deal of time-consuming and labor-intensive tasks in their daily work. Self-generated reports and maps provide a constantly updated overview of the IT network, enabling IT and business managers to make informed decisions. By constantly monitoring security-relevant systems, IT security officers can quickly track changes and ensure that all systems are up to date.
- Use cases
- Use cases
- Training
- Support
- Shop
- Partner
- Login