
March 23, 2022
Automatically detect orphaned user accounts
The things that turn out to be security-relevant in today’s IT world amaze many. Because ...


March 23, 2022
The things that turn out to be security-relevant in today’s IT world amaze many. Because ...

February 21, 2022
Let’s face it. Who among us has never written a password on a piece of ...

December 1, 2021
A modern IT system allows us to set all possible security measures in a finely ...

December 1, 2021
“PrintNightmare”, what is it actually? The Windows 10 exploit known as “PrintNightmare” is currently on ...

December 1, 2021
Back then… Can you still remember the telephone number databases on CD? With which we ...

December 1, 2021
A colourful world with weak points Threats in the IT sector have existed since IT ...

December 1, 2021
According to Dell Technologies’ Global Data Protection Index, around 80% of German companies faced major ...

January 10, 2020
The cloud is totally in vogue. No matter where you look in the IT industry, ...
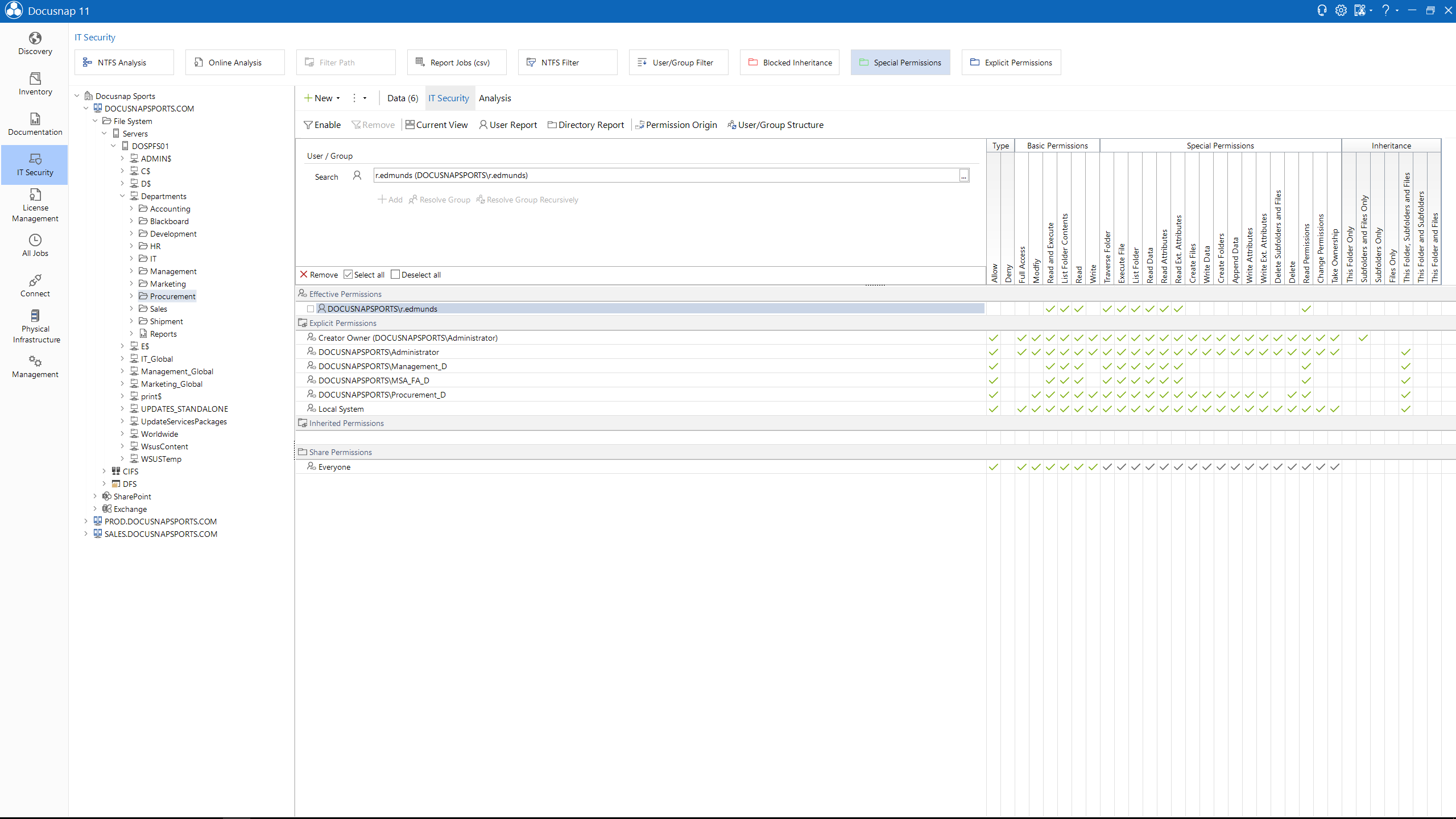
April 18, 2023
The other day at an appointment: The customer and I look at Docusnap’s authorization analysis ...
